GNSS 干扰可分为以下两类:
- 干扰
- 仿冒
干扰攻击是指在与 GNSS 相同的频段内广播强无线电信号,这可能会淹没 GNSS 卫星广播的相对较弱的信号。这可能会阻止 GNSS 接收器(包括手机)计算其位置。
欺骗是一种更复杂的攻击,在此期间会广播伪装成真实 GNSS 信号的虚假信号。这些虚假信号可能会欺骗 GNSS 接收器,使其计算出与实际情况相差很大的位置或时间,足以让地图和导航应用向用户提供错误信息。
关于 GNSS 欺骗或干扰
信号的信号强度或载噪比 (C/N0),以及手机中 GNSS 无线装置的自动增益控制 (AGC) 都可以很好地指示是否存在干扰。
当检测到欺骗或干扰时,AGC 往往会下降。当无线电接收到强无线电波时,它会调低放大器的增益 (AGC) 以调整接收信号的功率。
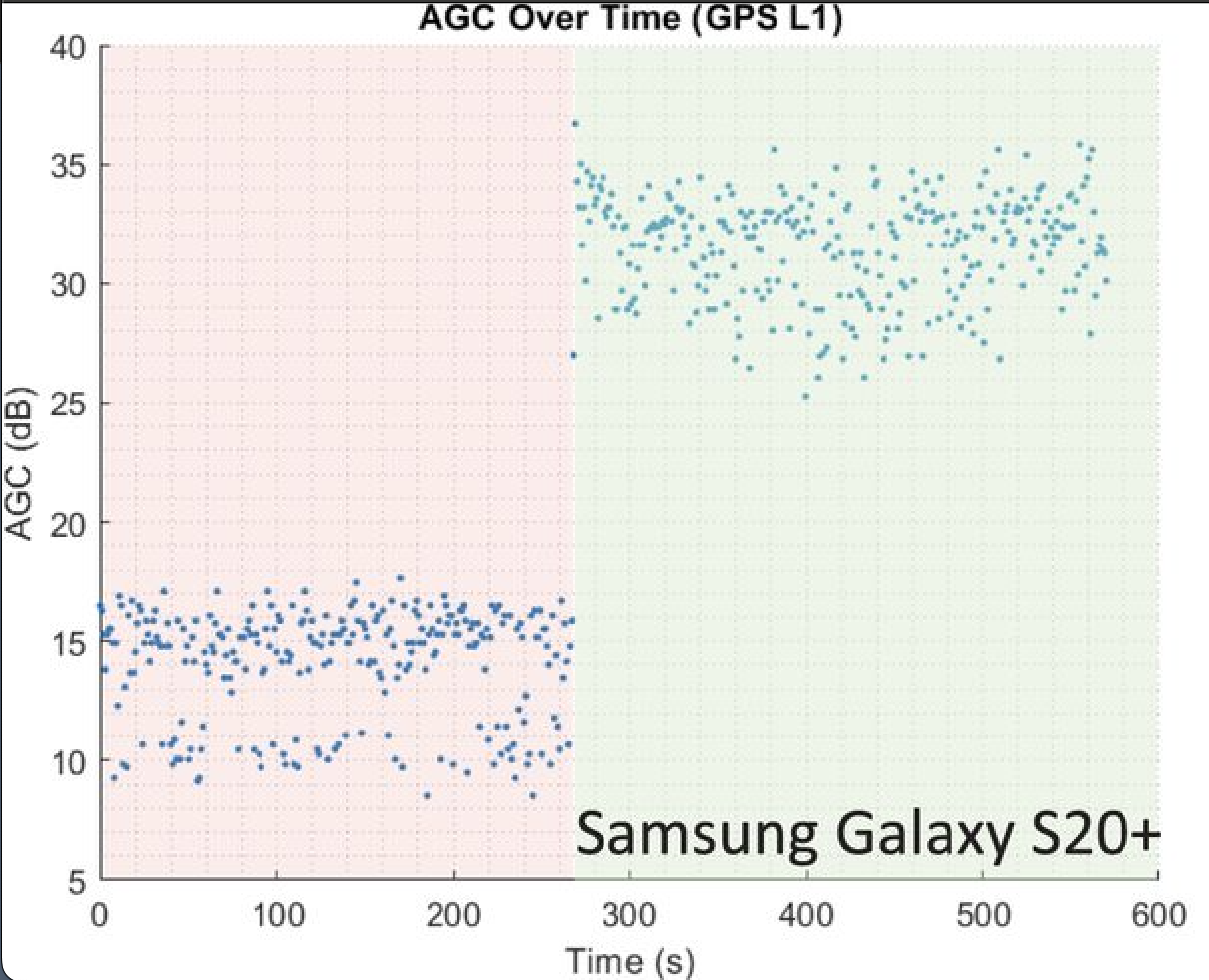
不过,在干扰事件和欺骗事件之间,C/N0 的行为会有所不同。对于干扰事件,无线电观测到的噪声比正常情况强得多,因此载噪比的分母会增加,而 C/N0 值会下降。对于欺骗,情况正好相反 - 由于广播的虚假信号足够强,可以淹没来自卫星的真实信号,因此总体信号强度很强,从而导致 C/N0 增加。
检查是否存在 GNSS 欺骗或干扰
您可以使用 GnssLogger 应用中的 Spoof/Jam 标签页,实时探索环境对 C/N0 和 AGC 的影响。
实时 AGC 和 C/N0 图
欺骗/干扰标签页会显示每个 GNSS 星座和频段(例如 “GPS L1”或“G:L1:”、“Galileo E5a”或“E:E5A:”。
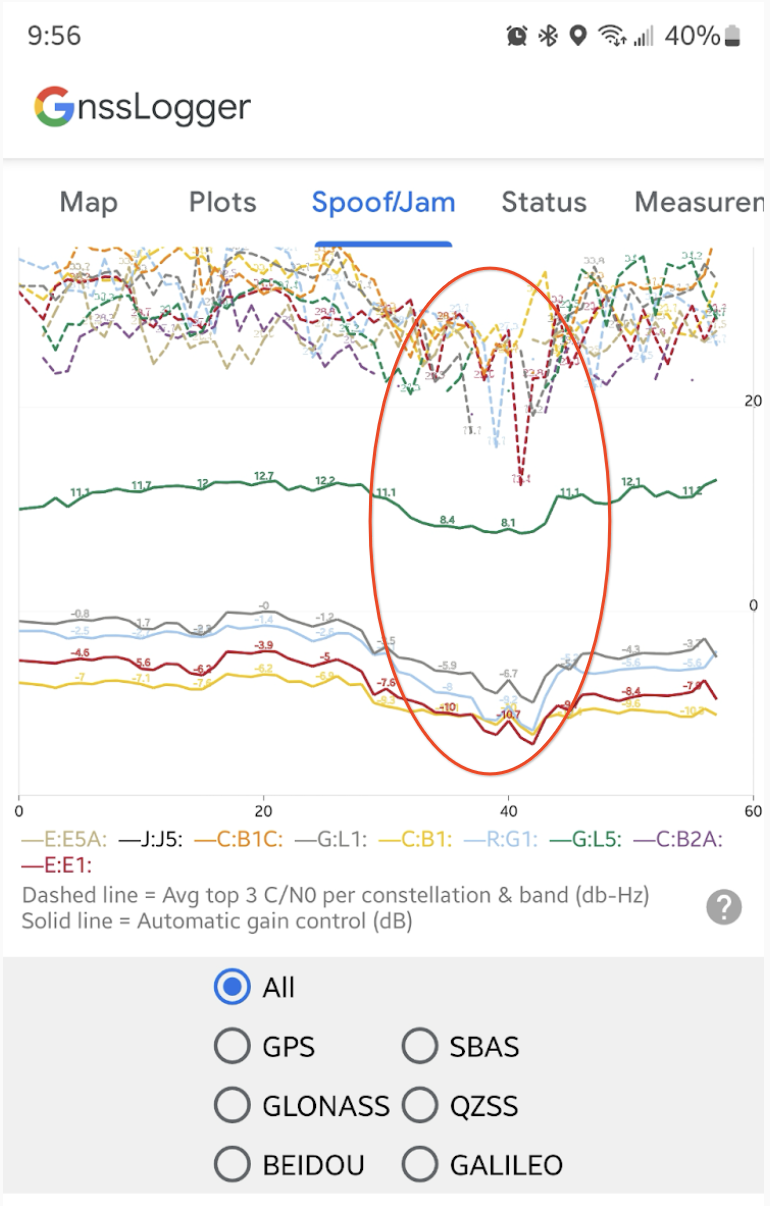
实时检查欺骗和干扰
在 AGC 和 C/N0 的实时曲线图下方,该应用会显示一系列自动数据检查,用于识别与 GNSS 干扰相关的条件。
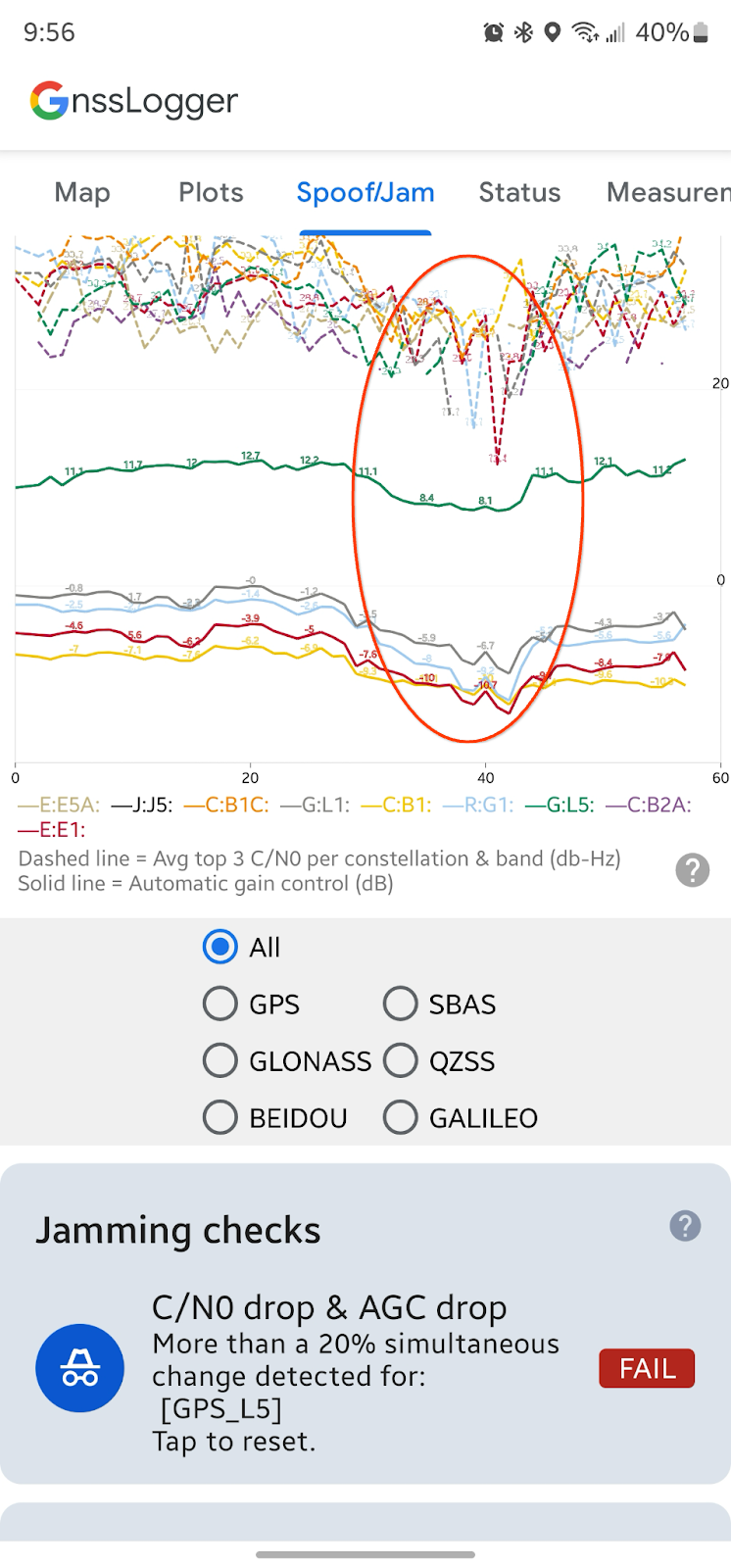
在干扰检查部分,应用会检查最近 10 个周期的 C/N0 和 AGC 的平均值与前 50 个周期相比是否发生了变化。如果 C/N0 和 AGC 同时降低,这可能是 GNSS 干扰的症状。如果检测到这种情况,该卡片会显示“失败”消息以及更多信息:
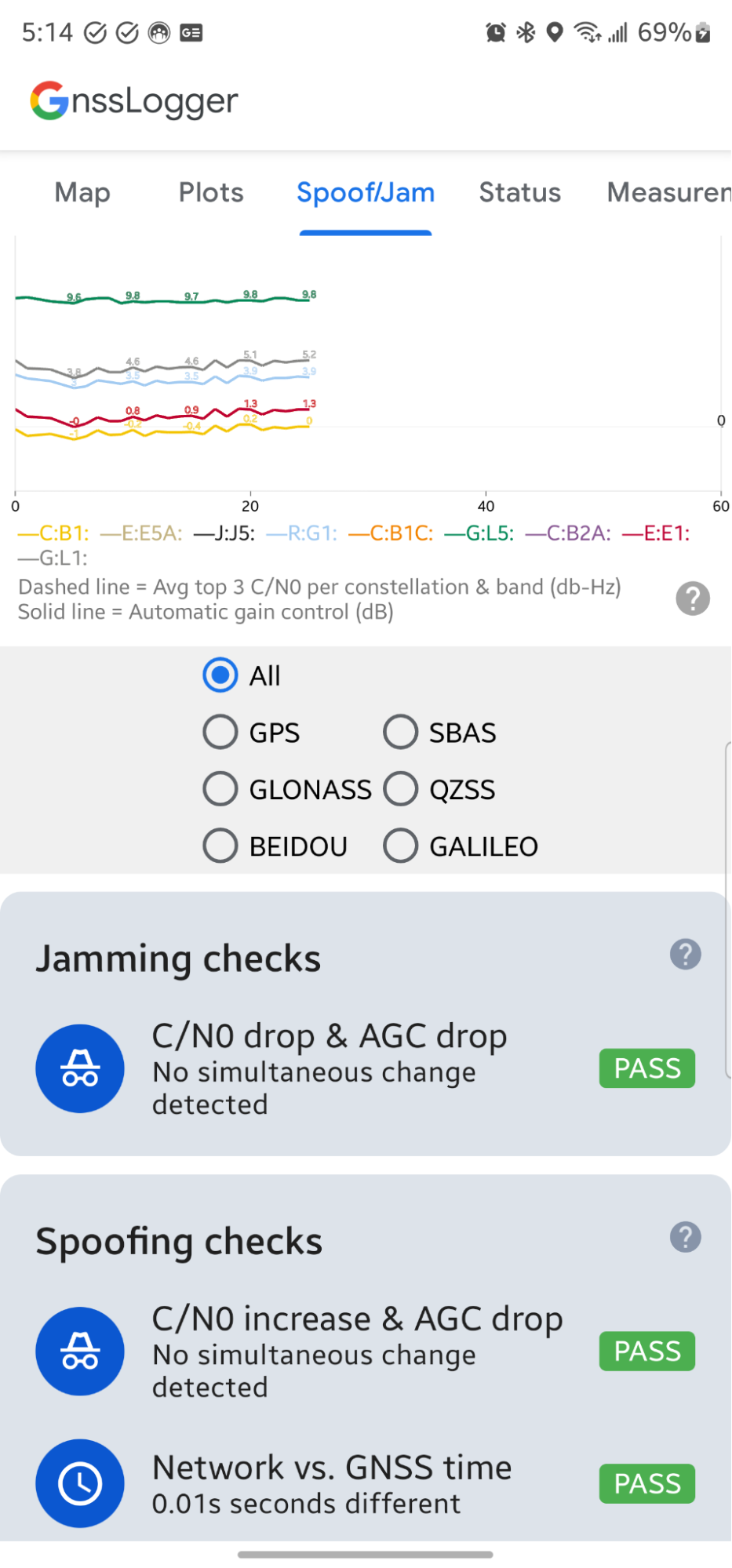
欺骗性检查部分中的第一张卡片也会检查 C/N0 和 AGC,但会查找 C/N0 同时增加且 AGC 下降的情况。
第二项与欺骗相关的检查会查找设备上计算出的 GNSS 时间与通过互联网从网络时间协议 (NTP) 服务器检索到的时间(网络时间 - GNSS 时间)之间是否存在超过 1 秒的差异。如果差值较大,可能表示计算出的 GNSS 时间无效。
提示、技巧和注意事项
使用 GnssLogger 的 Spoof/Jam 功能时,请注意以下事项:
- 这是一项实验性功能 - 随着我们对各种 Android 设备上的 AGC 特征的了解不断深入,用于欺骗和干扰的精确算法可能会更新。
- 此功能无法捕获所有欺骗和干扰行为 - 实时图表和数据检查可让您更轻松地实时发现数据属性,但不够强大,无法检测到所有欺骗或干扰行为。
- 此功能旨在检测 C/N0 和 AGC 的变化 - 如果您在存在欺骗或干扰的情况下打开应用,但 C/N0 和 AGC 保持不变,则系统不会检测到欺骗和干扰。
- NTP 服务器不一定安全,网络时间也可能会被欺骗。
使用我们的公开问题跟踪器就欺骗/干扰功能提供反馈。
